Azure Load Balancer Setup and Configuration
Once the Azure Load Balancer is create , Then search for Load balancer then select the load balancer.
Click on Overview:
Overview :
It will show all the Azure Network load balancer like Backed IP address, Health Probs Load Balancing rule, NAT rules Subscription ID and other Details.
Activities Logs:
Activities logs are the just like a events logs of your services or It will show complete activity logs on your Azure Network load balancer .
Access Control (IAM) :
It is Role based access authentication for Network load balancer , If you want some from you team to manage the Network load balancer or you want to restricts the access to other department that you can add that user in IAM and limited the access to particular user.
Tags:
Tags are name/value pairs that enable you to categorize resources and view consolidated billing by applying the same tag to multiple resources and resource groups.
Diagnose and Solve Problem:
It is MS azure Knowledge-base solution , It is collection of common scenarios solution where we can go through the solution and try to fix the issue Common Scenario are below and more you can find in azure portal.
- Load Balanced VMs are not receiving traffic
- VMs behind Load Balancer (LB) not responding to requests
- ADFS & SharePoint connections fail behind Load Balancer over VPN
- My issue is not listed
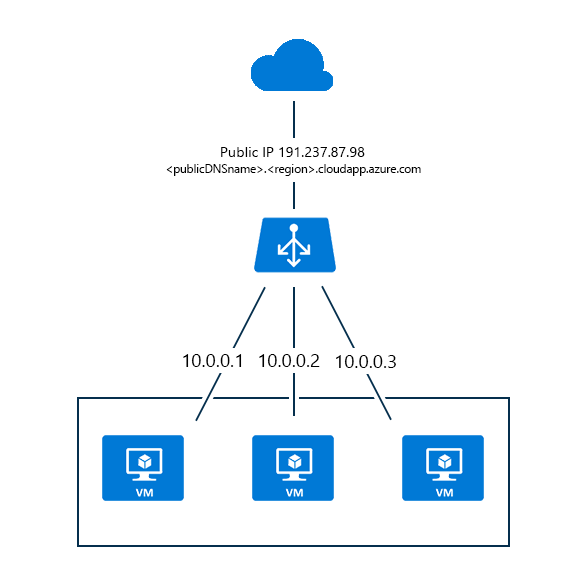
Azure load balancer Front End Pool:
Front end pool has public IP (PIP) addresses for incoming network traffic
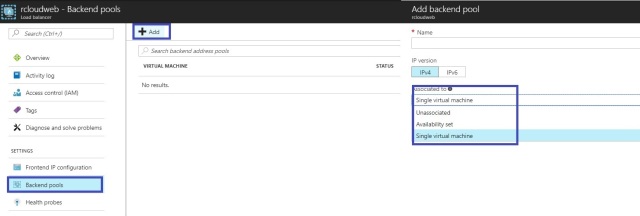
Back-end address pool:
- It contains network interfaces (NICs) for the virtual machines to receive network traffic from the load balancer.
- The virtual machine will be selected in the backend pool should be target for the load balance traffic of this rule.
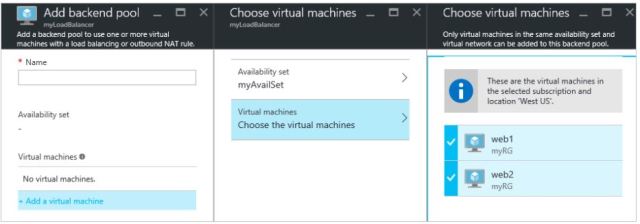
We can add the Vms in backend Pool as per below mention .
- Single Virtual Machine : We can add the Single Virtual Machine in Backend pool.
- Availability Set: Best Option which Microsoft suggested ,that We will add the Availability set in Azure load balancer which will provide the better reliability and performance for azure Load balancer.
When we will add the availability set , all the Vms will be added automatically as a part of availability set to Backend pool .
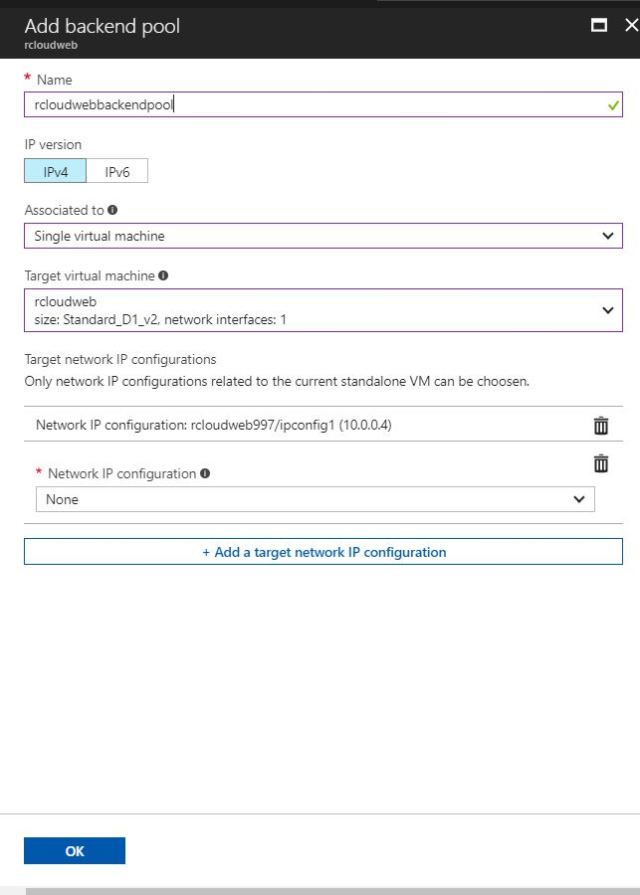
We will be able to see the below configuration if we are adding the Single VMs.
Please do set the Vms you want to add the VMs in backendpool.
We can select the Availability Set as per below configuration based on the requirements.
- Name : As per your organization standard .
- IP Version: IPv4 or IPv6
- Associated with Single Virtual Machine or Availability set.
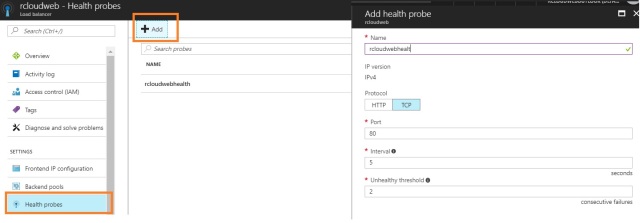
Health Probes :
Protocol: Load Balancer will work on HTTP or TCP protocol , Please select which protocol you want to route the traffic for your applications .
Port: You can select the port number where you want to allow the traffic and https port 443 or TCP port 80.
Interval: The amount of time between probs attempts
Unhealthy Threshold: The number of consecutive probe failures that must occur before a virtual machine is considered unhealthy.
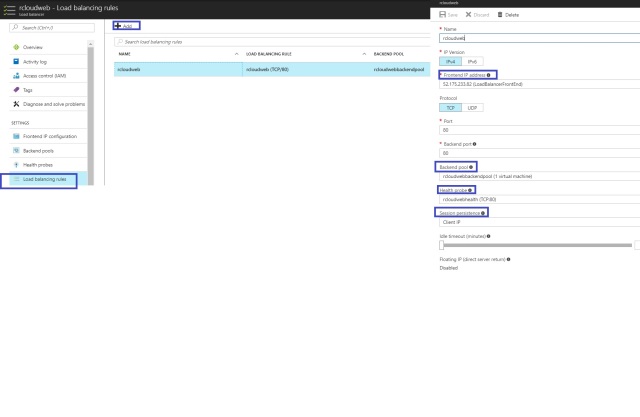
Load Balancing Rule
We can configure the Load balancing rule based on the application requirements.We can enable the below configuration for load balancing.
Interval: The amount of time between probs attempts
Unhealthy Threshold: The number of consecutive probe failures that must occur before a virtual machine is considered unhealthy.
Front End IP address: Client will communicate on load balancer on selected IP address services will have their traffic routes to the target machine by this NAT rule
Backend Port: You can choose to route traffic to the virtual machines in the backend pool using a different port than the one clients use to communicate with the load balancer.
Backend Pool: The virtual machine will be selected in the backend pool should be targeted for the load balance traffic of this rule.
Health Probe: The selected probe used by this rule to determine which virtual machine in backend pool are healthy and can receive load balanced traffic.
Session Persistence: Session persistence specifies that traffic from a client should be handled by the same virtual machine in the backend pool for the duration of a session”None: specifies that successive requests from the same client may be handled by any virtual machine:client IP” specifies that successive request form the same client IO address will be handled by the same virtual machine.
“Client IP and protocol” specifies that successive requests from the same client IP address and protocol combination will be handled by the same virtual machine.
Idle Timeout: Keep a TCP or HTTP connection open without relying on clients to send keep-alive messages.
Floting IP: We recommend using this feature only when configuring a SQL always on availability Group listener . It can be enabled only when creating a rule and if the port and a backed port matches.
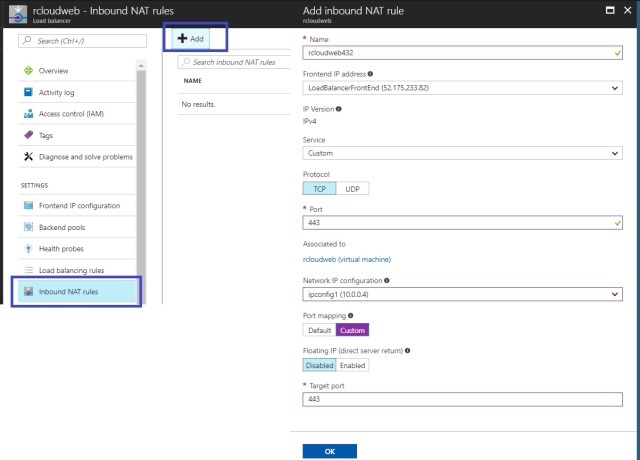
Inbound NAT Rules
Contains rules mapping a public port on the load balancer to a port for a specific virtual machine in the back-end address pool.
Name: Please provide the Name as per your organization Standard .
Frontend IP address: Client will communicate on load balancer on selected IP address and services will have their traffic routes to the target machine by this NAT rule
IP version: The IP version of the front end IP address must match the IP version of the target network IP configuration. Public load balances support IPv4 and IPv6. Internal load balancers support IPv4.
Network IP Configuration: The IP configuration that will receive traffic for the chosen Virtual machine. The IP version of the IP configuration much match the IP version of the front-end IP address.
Port Mapping:By default, traffic is routed to the target virtual machine on the same port that clients use to communicate with the load balancer. You can specify a custom port mapping to route traffic to a different port on the target virtual machine.
Services: We can select the custom services like HTTP, SSH,TCP MangoDB, Cosmos DB etc
Associated to : You can select the VM which you want to traffic should be route first on that Application based on the requirements.
Protocol :Based on your services you need to select the TCP/HTTP Protocol.
Port: Based on your services you need to select the TCP/HTTP port to route the traffic like port number 80 or 443 etc.
Network IP Configuration : It will be by default configure as per your VMs configuration and associated to Vms Internal IP address .
Port Mapping: If we want to Map custom of default port to our application we can select this option or let it default option selected.
Floting IP :We recommend using this feature only when configuring a SQL always on availability Group listener . It can be enabled only when creating a rule and if the port and a backend port matches.
Target Port: It will be same port you have configure your application and you have target the same port for traffic to route between applications.
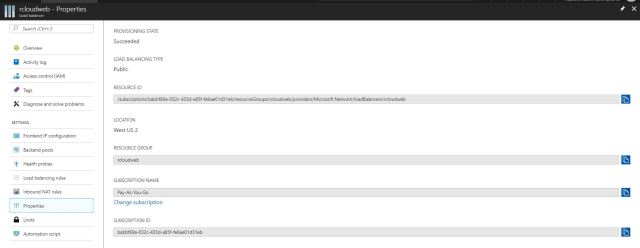
Properties :
IT will show where you are resources has been deployed and what is the configuration etc.
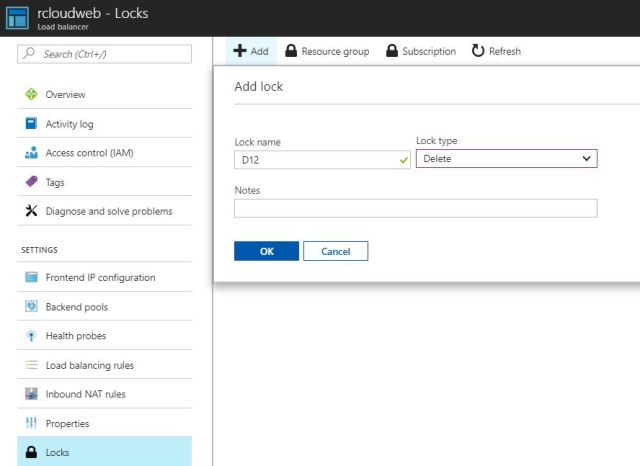
Lock
We can avoid the deleting the services while configuration of lock option.
Diagnostic Logs:-
It will shows your application logs and it will help to analyze the issue and troubleshoot further if there is any problem with the applications.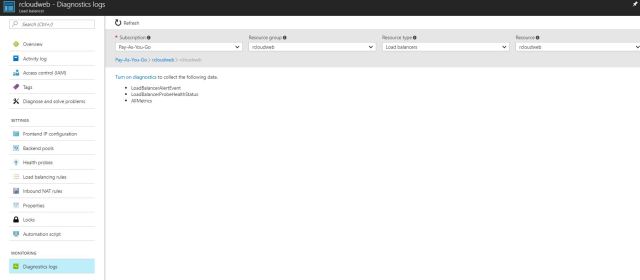
For Deep Drive Please do Refer Microsoft Azure Load Balancer Docs: PFB below link.