What is Site to Site VPN
Site-to-site VPN is a type of VPN connection that is created between on your azure and On-premises locations. It provides the ability to connect geographically separate locations or networks & usually over the public Internet connection or a WAN connection.
A Site-to-Site VPN gateway connection is used to connect your on-premises network to an Azure virtual network over an IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. this types of VPN connection required a VPN device located on-premises that has an externally facing public IP address assigned to it.
How to Create Site to Site VPN
Prerequisite: —
Verify Below Criteria before you will create the site to site connection:-
- Please Verify in which Azure model (Classic or Resource manager )you want to create the Site to site connection. These two models are not completely compatible with each other.
- Before we start the configuration and deployment we should know on which model we need to deploy as both the model are not compatible with each other.
- Microsoft has always recommend to use the Resource Manager deployment model.
- It’s very important point to verify the compatible VPN device which supports the Site to site, Multi site etc. VPN connectivity through route based protocol and Network Engineer who will configure this Device because MS has so many vendor who will provide the their image.
- We required an externally facing public IPv4 IP address for our VPN device. This IP address cannot be located behind a NAT.
- If we are not unfamiliar with the IP address ranges located in your on-premises network configuration, Please coordinate with your network administrator who can provide the IP Range, Subnet and other required details.
- When We create this configuration, We must specify the IP address range prefixes that Azure will route to your on-premises location.
- None of the subnets of our on-premises network can overlap with the virtual network subnets that we want to connect .
Step: 1:- Create Virtual network using below link.
To create Teh Vnet we should have below required details and if you are working with project then please contact your network administrator before you will proceed further.
Below things are optional and it is not related to any network , For example i will provide the details
- Virtual Network Name: Rcloud
- Address Space Range:
- 10.30.10.0/16
- 10.14.0.0/16 (optional for this exercise)
- Subnets:
- FrontEnd: 10.30.10.0/24
- BackEnd: 10.14.0.0/24 (optional for this exercise)
- Subnet Gateway: 10.31.255.0/27
- Resource Group: Rcloud
- Location: East US
- DNS Server: We can choose the default IP address of DNS serve till the time you didn’t integrate your VPN to Azure.
- Virtual Network Gateway Name: Rcloud
- Public IP Name: VNet1GWIP
- VPN Type: Route-based
- Connection Type: Site-to-site (IPsec)
- Gateway Type: VPN
- Local Network Gateway Name: Rcloud1
- Connection Name: Azure to On premises
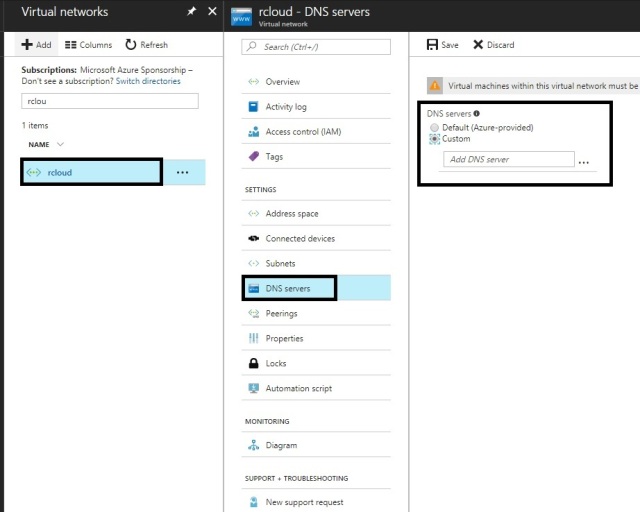
Step2: Specify a DNS server
DNS is not required to create a Site-to-Site connection. However, if we want to have name resolution for resources that are deployed to your virtual network.
We should specify a DNS server either Default or On-premises DNS Server.
This setting lets us specify the DNS server that we want to use for name resolution for this virtual network.
Step 3: Create the gateway subnet
Virtual network gateway uses specific subnet called the ‘GatewaySubnet’. The gateway subnet contains the IP addresses that are used by the VPN gateway services.
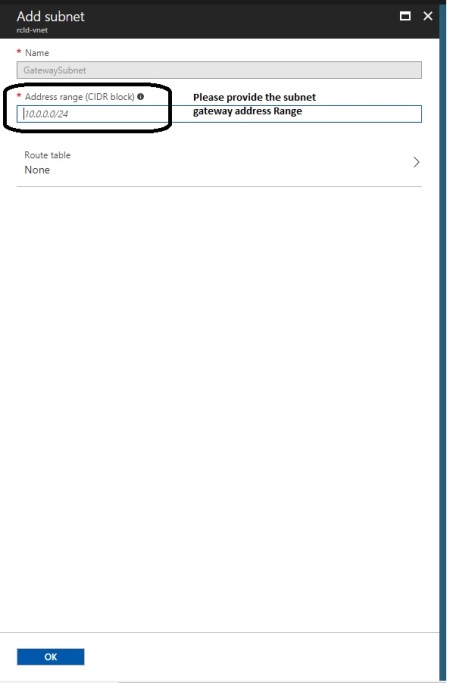
- When we create a gateway subnet, it must be named ‘GatewaySubnet’. Naming a subnet ‘GatewaySubnet’ tells Azure where to create the gateway services.
- If we name the subnet something else, Our VPN gateway configuration will fail.
- The IP addresses in the GatewaySubnet are allocated to the gateway services. When we create the GatewaySubnet, We specify the number of IP addresses that the subnet contains.
- The size of the GatewaySubnet that we specify always depends on the VPN gateway configuration that we want to create.
- Hence it is possible to create a GatewaySubnet as small as /29 and Microsoft recommend that we can create a larger subnet that includes more addresses by selecting /27 or /28.
- Using a larger gateway subnet allows for enough IP addresses to accommodate possible future configurations.
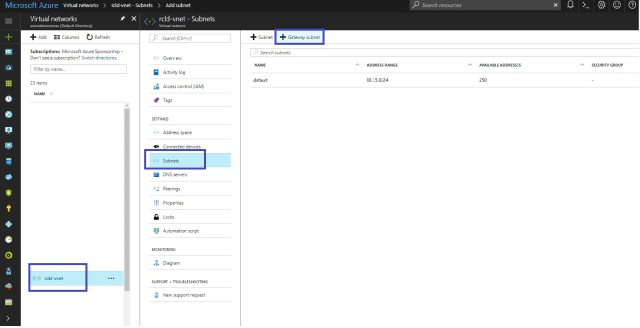
- In Azure portal, navigate to the virtual network for which you want to create a virtual network gateway.
- In the Settingssection of your VNet blade, click Subnets to expand the Subnets blade.
- On the Subnetsblade, click +Gateway subnet at the top. This will open the Add subnet
Add the Subnet gateway
Step-4: Create a VPN Or Virtual Network gateway.
Prerequisite :-
Virtual Network Gateway name: Please provide the Virtual network name your organization naming convention.
Gateway Type : Vnet gate way are 2 Types. It is basically how you wan to connect to your on-premises VPN devices.
VPN Types are :–
Site to Site :
A Site-to-Site (S2S) VPN gateway connection is a connection over IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. S2S connection requires a VPN device located on-premises that has a public IP address assigned to it and is not located behind a NAT.
S2S connections can be used for cross-premises and hybrid configurations.
Note: It is connection over the Public IP which extend your data center using the VPN device to Azure.
- Point to site :A Point-to-Site (P2S) VPN gateway connection allows you to create a secure connection to your virtual network from an individual client computer. P2S is a VPN connection over SSTP (Secure Socket Tunneling Protocol).
Note: It is a connection where you can connect your Azure VMs useing a VPN connection.
- Express Route : Microsoft Azure Express Route lets you extend your on-premises networks into the Microsoft cloud over a dedicated private connection facilitated by a connectivity provider
Note: It is private connection from your datacenter to Azure by Dedicated private Facilitated by your ISP which will allow O365,O365 Dynamics MS azure or cloud services connect directly using as Site to site or Point to Site connectivity.
| Services | Point-to-Site | Site-to-Site | ExpressRoute |
| Azure Supported Services | Cloud Services and Virtual Machines | Cloud Services and Virtual Machines | Public Peering Power BI Dynamics 365 for Operations (formerly known as Dynamics AX Online) Most of the Azure services with a few exceptions below CDN Visual Studio Team Services Load Testing Multi-factor Authentication Traffic ManagerMicrosoft peering Office 365 Dynamics 365 (formerly known as CRM Online) Dynamics 365 for Sales Dynamics 365 for Customer Service Dynamics 365 for Field Service Dynamics 365 for Project Service |
| Typical Bandwidths | Typically < 100 Mbps aggregate | Typically < 1 Gbps aggregate | 50 Mbps, 100 Mbps, 200 Mbps, 500 Mbps, 1 Gbps, 2 Gbps, 5 Gbps, 10 Gbps |
| Protocols Supported | Secure Sockets Tunneling Protocol (SSTP) | IPsec | Direct connection over VLANs, NSP’s VPN technologies (MPLS, VPLS,…) |
| Routing | RouteBased (dynamic) | We support PolicyBased (static routing) and RouteBased (dynamic routing VPN) | BGP |
| Connection resiliency | active-passive | active-passive or active-active | active-active |
| Typical use case | Prototyping, dev / test / lab scenarios for cloud services and virtual machines | Dev / test / lab scenarios and small scale production workloads for cloud services and virtual machines | Access to all Azure services (validated list), Enterprise-class and mission critical workloads, Backup, Big Data, Azure as a DR site |
SKU: Below are SKU are provided by Microsoft team.
| SKU | S2S/VNet-to-VNet | P2S | Aggregate |
| Tunnels | Connections | Throughput | |
| VpnGw1 | Max. 30 | Max. 128 | 500 Mbps |
| VpnGw2 | Max. 30 | Max. 128 | 1 Gbps |
| VpnGw3 | Max. 30 | Max. 128 | 1.25 Gbps |
| Basic | Max. 10 | Max. 128 | 100 Mbps |
Public IP : We have create the new public IP address which will be use for virtual network gateway . Please provide the name as per your organization naming convention.
Subscription : Under which subscription you need to create the Vnet gateway
Resources Group :You Resource Group name under you have created teh Virtual Network
Location: Location of your VPN devices location or near to your data center.
1: Go to search Button and search Virtual network gateway
Click on Add Virtual Network.
Provide the Configuration As per your organization required.
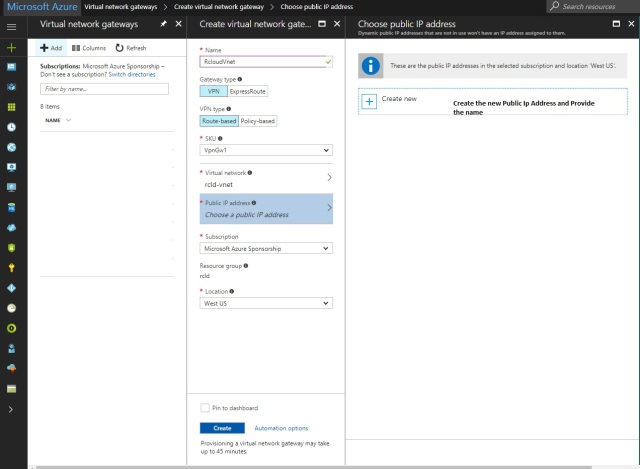
Click Create and it will take around 45 min to complete.
Step-5: Create the Local Network Gateway
Local network gateway refers to your on-premises location.which gives you site name which you can specify in azure ,Than specify the IP address of the on-premises VPN device to where you will create a connection. we also specify the IP address prefixes that will be routed through the VPN gateway to the VPN device.
The address prefixes you specify are the prefixes located on your on-premises network. If we have on-premises network changes or we need to change the public IP address for the VPN device, we can easily update the values later.
- In the portal All resources, click Add Button
- Click Networking – Select – Local network gateway, then click to search. This will return a list. Click Local network gateway to open the local network gateway properties, then click Create to open the Create local network gateway .
- Please provide the Public IP Address of your RAAS Device or VPN Device IP
- Just type on Google What is my IP you will get the Public IP address. this is recommend only for testing purpose RAAS device.
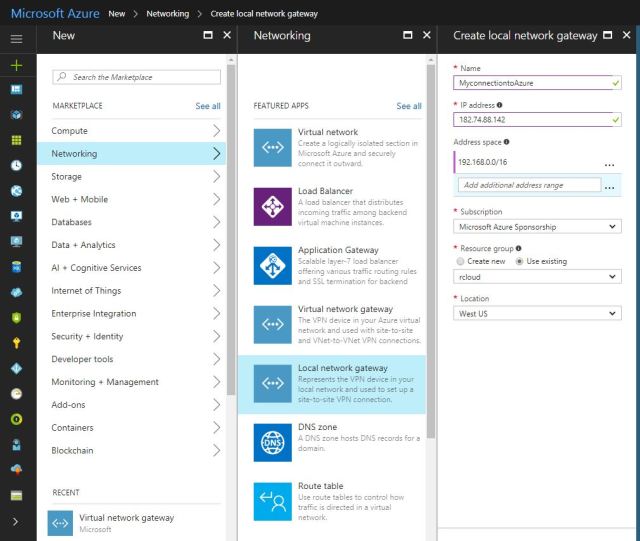
- Click on Create , Once the Local network created please configure the VPN device and configure the Site to site connection using the local network gateway and virtual network gateway.

It’s very strate foword article ,now I am I will be able to create v net as after understanding the vnet configuration from this blog. You are really putting the short and quantitiv information.
Thanks again.
LikeLiked by 1 person
Pingback: Azure Interview Q & A-part1 – RCloud