What Azure Virtual Networks ?
Azure Virtual Networks is secure way to connect Azure resources & each other with virtual networks (VNets).A VNet is a represent of your own network in the cloud.
VNet is a logical isolation of the Azure cloud dedicated to your subscription. We can also connect VNet to our on-premises network.
Azure Virtual Network capabilities
- Isolation:
VNets are isolated & We can create separate VNets for development, testing, and production using the same CIDR address blocks. We can create multiple VNets that use different CIDR address blocks and connect networks together. We can segment a VNet into multiple subnets. Azure provides internal name resolution for VMs and Cloud Services role instances connected to a VNet. We can optionally configure a VNet using our DNS servers, instead of using Azure internal name resolution.
“CIDR : Classless Inter-Domain Routing, called as super-netting is a way to allow more flexible allocation of Internet Protocol (IP) addresses than it was possible with the original system of IP address classes or Basically it defines the range of IP address.”
- Internet connectivity:
Azure VMs and Cloud Services role instances connected to VNet, so they have access to the Internet and We will enable the inbound access to specific resources based on requirements.
- Azure resource connectivity:
Azure resources such as Cloud Services and VMs can connect to the same VNet. The resources can connect to each other using private IP addresses, even if they are in different subnets.
Azure provides default routing between subnets, VNets, and on-premises networks, so we don’t have to configure and manage routes.
- VNet connectivity:
VNet can be connected to each other & connect to any VNet to communicate with any resource on any other VNet.
- On-premises connectivity:
VNet can be connected to on-premises networks through private network connections between our network and Azure,or through a site-to-site VPN connection over the Internet.
- Traffic filtering:
VM and Cloud Services instances role can be filtered inbound and outbound traffic by source IP address and port, destination IP address and port,and protocol in network traffic.
- Routing:
You can optionally override Azure’s default routing by configuring your own routes,or using BGP routes through a network gateway
How to Create the Virtual Networks ?
- Please logging to the Azure portal & if you don’t have azure portal than please,
sign up for a free one-month trial.
- Click on the New (Plus Tab)
- Select networking
- Select the virtual network
- Please provide the Virtual Network Name
- Address Spaces (The virtual network’s address range in CIDR notion) – Please ask your network administrator to provide the Address space if you are planning to configure in Production Environment.
- Pleas Provide the Subnet name as per your requirements because you might be remember during the VPN configuration or VM creation.
- Subnet Address range:The subnet’s address range in CIDR notation.It must be contained by the address space of the virtual network. The address range of a subnet which is in use can’t be edited .
- Note: Please ask your network administrator to provide the Address space if you are planning to configure in Production Environment.
- Subscription Name
- Resource Group name :- Pleas keep all the resource in the same Resource group so while creating the S2S ,P2S etc VPN it will work fine.
- location : Please select the location as per your nearest region
- Click on Create and wait for 5 to 10 minutes.
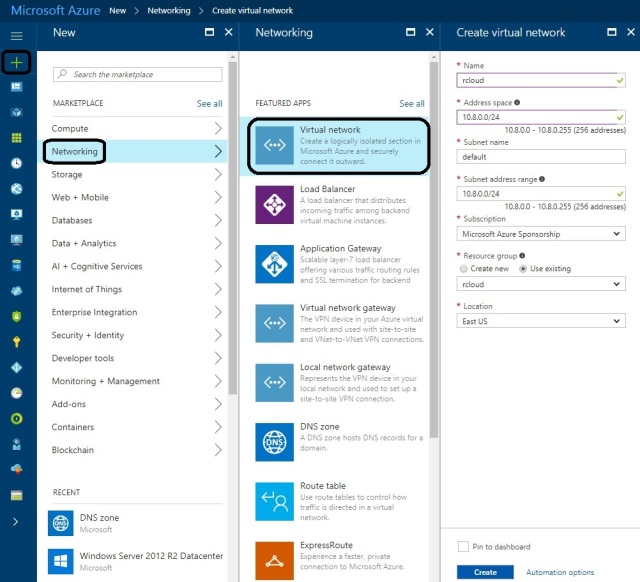
- Once it is created it will be looks like below.
- Please check the Vnet Properties and configuration.
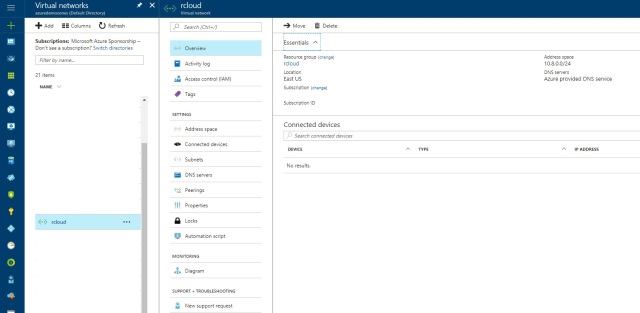
Overview: In overview tab it will show the address range ,location,subscription and other related details of your Vnets.
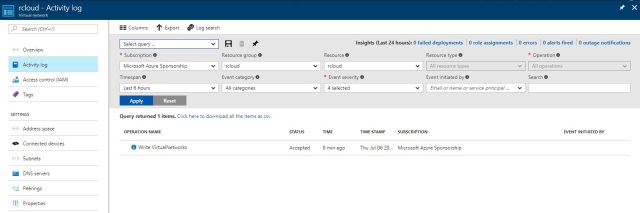
Activity Logs
Tags:Tags are name/value pairs that enable you to categorize resources and view consolidated billing by applying the same tag to multiple resources and resource groups
Address Spaces : The virtual network’s address range in CIDR notion
Connected Devices: This tab will show how many devices or services are connected to this V-net.
Subnets: We can add the addition subnet if it is required and we can Subnet gateway to create the site to site VPN.

DNS Servers: We can add the default or custom domain server as per our requirements.
Peering: Enables resources connected to different Azure VNets within the same Azure location to communicate with each other. The bandwidth and latency across the VNets is the same as if the resources were connected to the same VNet.
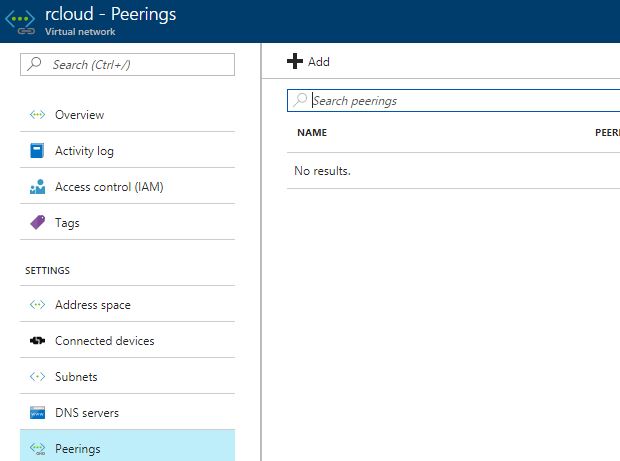
We can add the peer network as per our requirements.
- Provide the Name
- peer Details (ARM or ASM)
- Subscription ID
- Virtual Network apart form your network or Vnet yo want to peer.
- Enable the configuration Allow forward traffic/gateway Transit/Remote gateway.
Properties: It will show your properties of you Vnet.

Locks: In this tab we can lock the resource Group of Vent group for deleting/Editing.

Automation Script: It is used to deploy Vnet with ARM script.
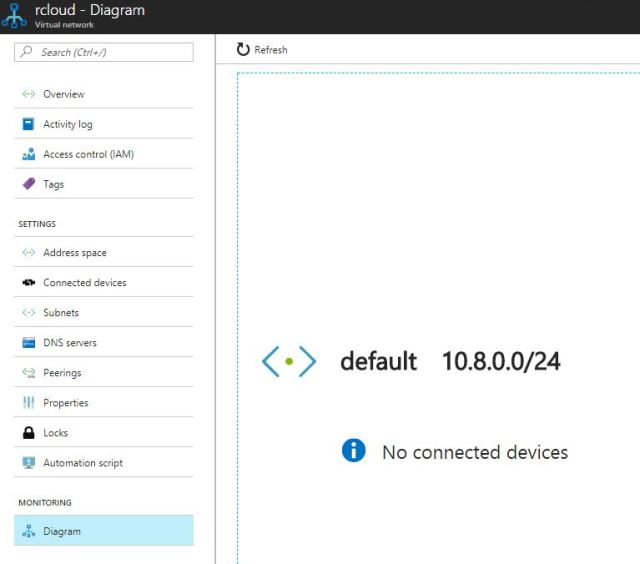
Diagram : This will show how many devices are connected .
Note:- I will cover Site to site VPN in next Blogs. Please do like and comments if you like the blog.

Good evening sir !
We are creating two vnets in different regions and different storage account s in global example 1.vnet in East us and 2. Vnet in South India by using vpn it is any possible to connect the two different virtual networks .
LikeLiked by 1 person
Yes it is possible , While creating the Vnet to Vnet configuration, Which i will be covering in my next session.
I will be explaining in details, So u can understand S2S,P2S and V2V how to create and use.
LikeLike
Thank u sir!
nice explansion.
LikeLike
Yes you need to create a VPN between them suing your vnet gateways
LikeLike
Yes without vnet gateway it will not connect
LikeLike
Nice Article, eager to see next sessions
LikeLiked by 1 person
Sure, Need some time
LikeLike
Nice article, I learn a lot form this. Thanks for make such a beautiful Azure documents.
LikeLike
Pingback: Azure Interview Q & A-part1 – RCloud